Introducing pucktools.com: The future of egress Testing for Stronger Network Security
Brought to you by Offensive Context based on 20 years of experience in penetration testing, red teaming, offensive tooling, and vulnerability research.
The Recurring Problem of Network Egress
In two decades of offensive security work, one pattern has stood out: outbound network controls (“egress”) are often weaker than organizations assume. Time and again, during penetration tests and red team engagements, I've found ways to quietly send data out of a "secure" network. Many companies confidently claim their firewalls block all unauthorized outbound traffic, only to discover hidden gaps. In practice, egress controls that look strong on paper may have misconfigurations or overlooked channels.
Attackers know this – they routinely exploit outbound paths for command-and-control (C2) and data exfiltration when infiltrating a network. Unfortunately, many defenses focus on stopping intrusions at the front door (ingress) while the back door (egress) remains ajar.
The reason this issue keeps appearing is often overconfidence in network policy versus actual enforcement. An organization might, for example, restrict servers to only web browsing ports, but if one forgotten server can reach the internet on an unexpected port or use DNS in a crafty way, an attacker can slip out undetected. Assuming your egress is locked down is risky – you need to validate it.
Don't Assume – Continuously Verify Your Defenses
It's not enough to set egress firewall rules once and forget them. Networks are dynamic – new systems come online, cloud services spin up, developers open ports for troubleshooting, or updates alter firewall settings. A rule that worked last month might be inadvertently changed today.
Continuous monitoring and validation of network defenses is essential. Just as we employ continuous integration and testing in development, our security controls need continuous testing. Without ongoing checks, an organization might go months assuming "no news is good news," only to find out that a misconfigured firewall has been quietly allowing outbound traffic all along.
Introducing pucktools.com – Your Egress Safety Net
To address this challenge, I helped created pucktools.com, a platform purpose-built to continuously test and monitor outbound network controls. Puck was born from the frustration of seeing organizations caught off-guard by egress weaknesses that were assumed to be under control.
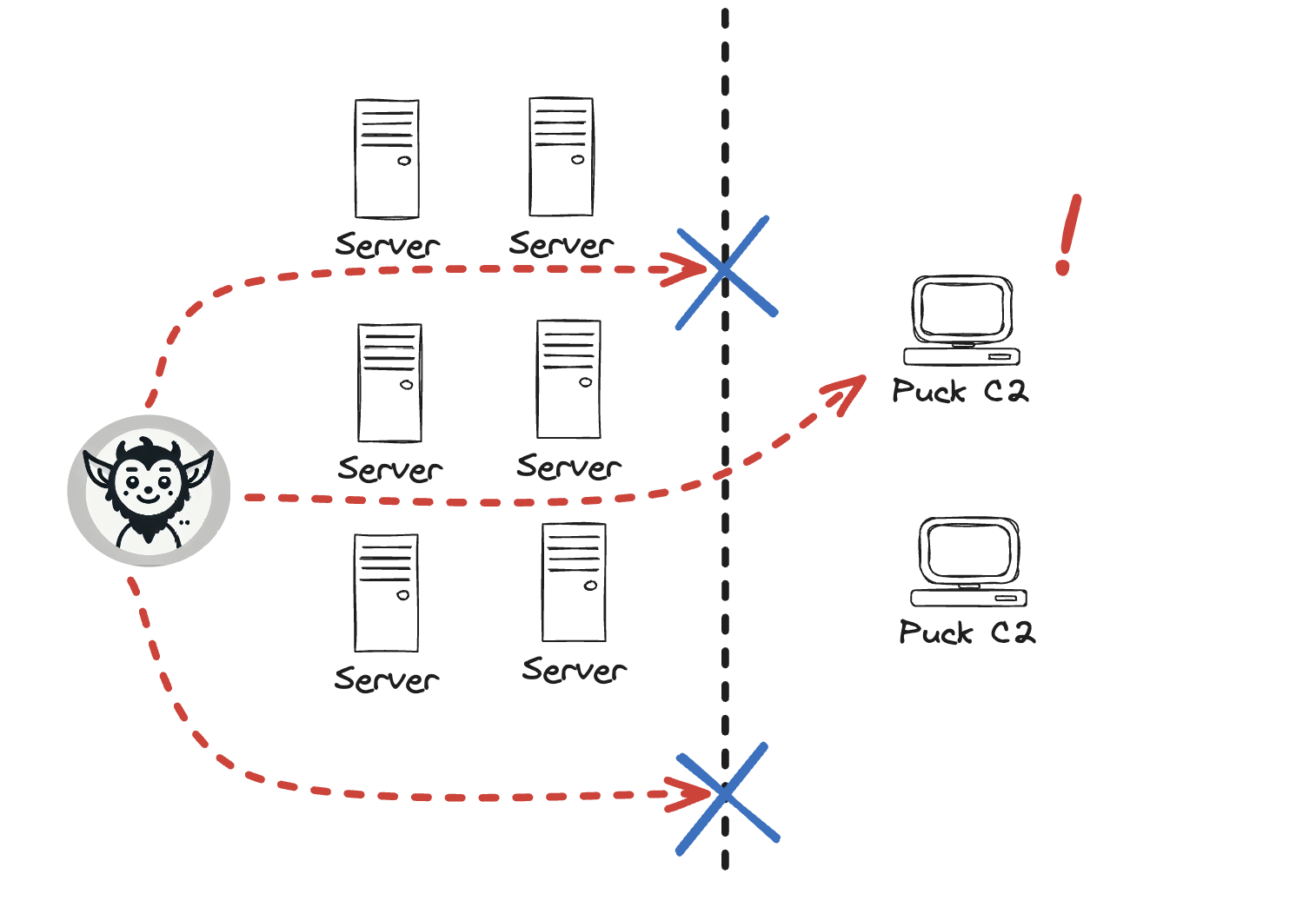
At its core, pucktools.com is a specialized security platform designed to uncover network leaks by testing egress paths. In practical terms, you deploy a small Puck agent inside your network (think of it like dropping a test beacon behind your firewall). Once deployed, the puck systematically tries to connect out to our managed command-and-control (C2) servers using various protocols commonly abused by attackers.
It safely emulates the techniques real malware might use, attempting to open outbound channels for C2 or data exfiltration. Crucially, these tests use dummy data and occur in a controlled manner – the Puck agent is not accessing any of your sensitive files or running any rogue commands on your systems. Its sole job is to repeatedly probe your egress defenses, just as an attacker would, but without the danger.
The beauty of this approach is that it flips the script on attackers. Instead of waiting to discover a breach the hard way, pucktools.com proactively finds any egress "leaks" and alerts you right away. If a Puck agent manages to establish an outbound connection over, say, DNS or an uncommon TCP port that should have been blocked, you (and your team) will get an immediate notification. This early warning gives you a chance to close that escape route before a real attacker exploits it.
Key Benefits of pucktools.com for Egress Security
pucktools.com was created with simplicity and effectiveness in mind, so that organizations can bolster their egress security without heavy lift. Here are some of the key benefits and features:
-
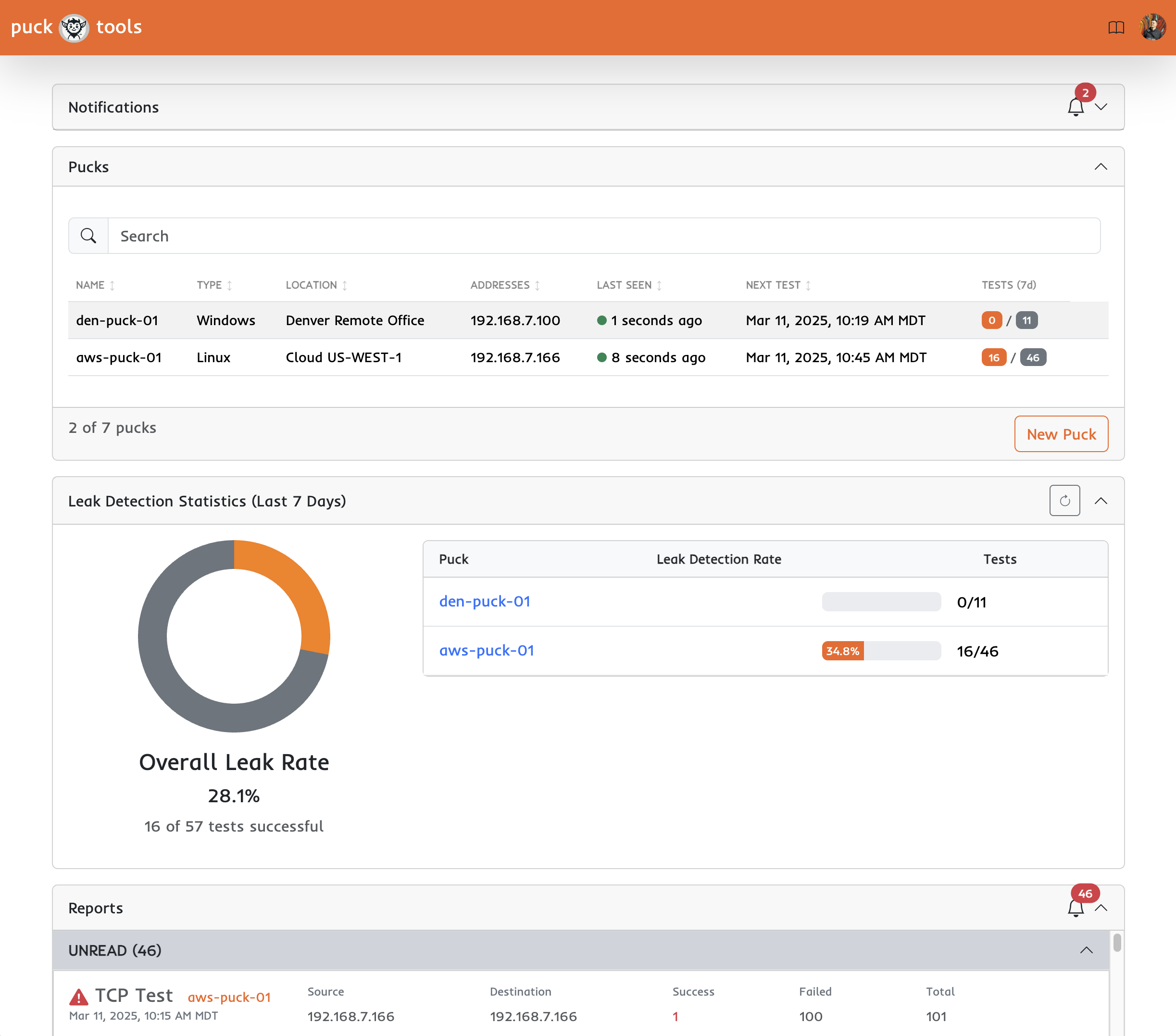
Continuous Egress Testing & Monitoring: Puck continuously enumerates common outbound channels and ports that attackers might use (for C2 or exfiltration) to ensure nothing is inadvertently left open. If something changes and opens up a new path, Puck will catch it.
-
Multi-Protocol Coverage: Attackers can abuse various protocols (HTTP(S), TCP, UDP, DNS, etc.) to get data out. Puck automatically tests outbound connectivity over multiple protocols and ports. Even non-standard or lesser-known egress channels are examined.
-
Real-Time Alerts on Leaks: If Puck finds a way out, it lets you know immediately. You receive alerts whenever an egress path is successfully established that shouldn't be. These real-time notifications mean your security team can react quickly.
-
Easy Deployment, Flexible Integration: Puck can be deployed as a small physical device, lightweight software on an existing server, or a container in the cloud. There are no complex remote servers to manage – the platform's managed C2 handles the heavy lifting.
-
Safe and Non-Disruptive Operation: The Puck agent won't scan your internal network or tamper with data. All communication tests are performed in a controlled, read-only manner. Puck provides assurance without causing performance issues or risking any sensitive information.
-
Validating Your Controls & Segmentation: By using Puck, you're effectively unit testing your firewall rules and network segmentation. It highlights misconfigurations and helps confirm that zones are properly isolated.
-
Clear Reporting and Insight: The platform provides dashboards and detailed reports to help communicate findings to both technical staff and high-level stakeholders. Over time, you can demonstrate measurable improvements.
Proactive Defense Through Validation
The ultimate goal of pucktools.com is to enable proactive defense. In today's threat landscape, it's not enough to simply set defenses and hope for the best – you need to continuously validate that those defenses actually work. This is especially true for network egress, where a single overlooked opening can be all an attacker needs to quietly exfiltrate critical data.
By regularly simulating outbound attack patterns, Puck lets your blue team and IT staff operate with an "assume breach" mindset: Assume an attacker might already be inside and trying to phone home, and make sure nothing gets out.
For CISOs and security managers, this kind of continuous validation is a powerful addition to your security program. It provides evidence-based assurance that your investments in firewalls, proxies, and network segmentation are holding strong. It shifts the narrative from reactive to proactive security.
DevOps teams also benefit. As they deploy new applications or infrastructure, Puck's continuous egress testing can serve as an automated safety net that catches misconfigurations early.
Conclusion: Don't Leave the Back Door Open
Network egress may not always grab headlines, but it is a critical part of any organization's security posture. As an offensive security veteran, I've learned that what you don't monitor can hurt you.
pucktools.com was built to shine a light on this often-neglected area, giving security teams an easy and continuous way to ensure that the "back door" of their network is as secure as the front. By continuously testing and validating outbound controls, organizations can move from assumption to certainty – knowing that their egress policies are not just on paper but enforced in reality.
In summary, pucktools.com helps you find and fix outbound network leaks before attackers do. It brings a simple yet powerful concept to life: continuous validation of your network defenses.
For CISOs, IT professionals, DevOps engineers, and blue teamers alike, it's a high-level solution that provides peace of mind without adding complexity. In a world of evolving threats, taking a proactive stance on egress security is a smart move – and with tools like Puck, it's also an achievable one.
Secure your outbound pathways, stay alerted to any weaknesses, and rest easier knowing you've locked the back door for good.
Sound good? Get Started or try a free egress test here