Who watches the watcher?
In security, we often operate on assumptions — that the tools we deploy are working, that policies are enforced, that configurations persist. But how often do we actually verify?
Recently, while developing a simple browser test scan, I got a stark reminder of why assumption validation isn't just important — it's essential.
Building a Test, Catching Myself
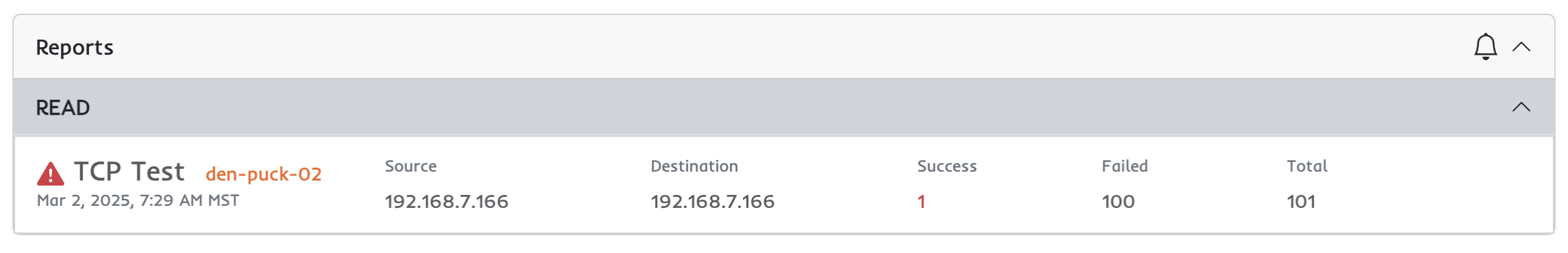
Puck is a new and simple way to automatically test egress filters, designed to automatically look for network leaks and ensure ports are blocked the way you expect them to be. While developing the scan feature, I started testing assuming all my firewall configurations had me covered.
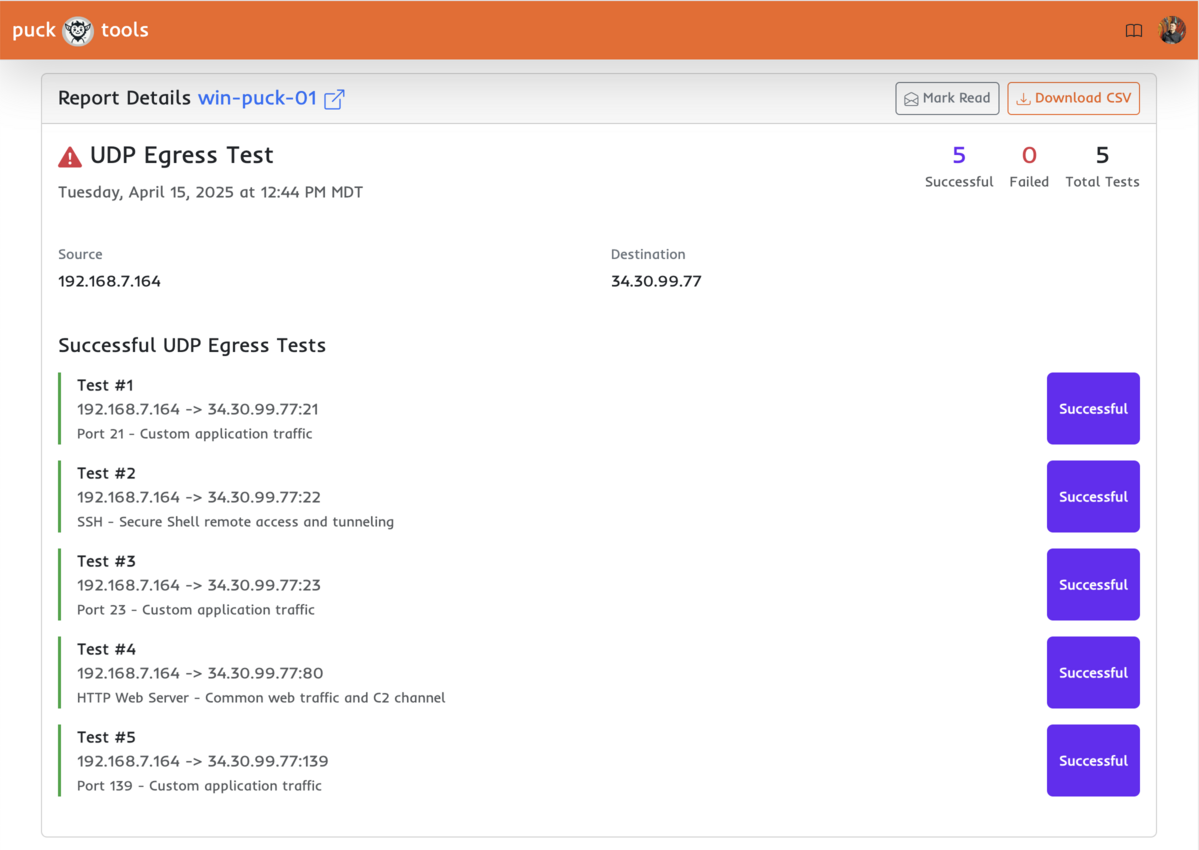
Except… they didn't.
The test flagged several ports open that absolutely shouldn’t have been. My immediate assumption was that my code was buggy. It’s new, after all. After some digging, I realized: the tool was right. My firewall wasn’t blocking those ports because — surprise — it wasn’t even enabled.
What Went Wrong?
I recently upgraded my laptop and as part of that upgrade after I restored my configs, I missed enabling my firewall. I never noticed, because I assumed it was still running. And every internal mental model I had about my system’s exposure was based on that faulty assumption.
The Bigger Lesson
Tools like Puck are great for uncovering external exposures, but they’re just as valuable for uncovering blind spots in our own thinking. This was a test I wrote to validate the tool, and it ended up validating something much more important: the need to continuously verify what we believe to be true.
Validate Everything
Security isn’t just about preventing threats — it’s about ensuring your defenses are actually in place. Even the best tooling can’t help you if you make decisions based on outdated or unchecked assumptions.
Ask the awkward questions. Rerun the tests. Validate your assumptions.
Who watches the watchers?
You do. Puck is here to help.