Understanding the Puck Agent
What is a Puck?
Puck is a specialized agent designed to safely emulate malware communication patterns in order to identify potential egress paths from your network. Puck does this by systematically testing outbound connectivity using techniques similar to those employed by actual malware, the Puck Agent helps security teams discover and remediate network security gaps before they can be exploited by real threats.
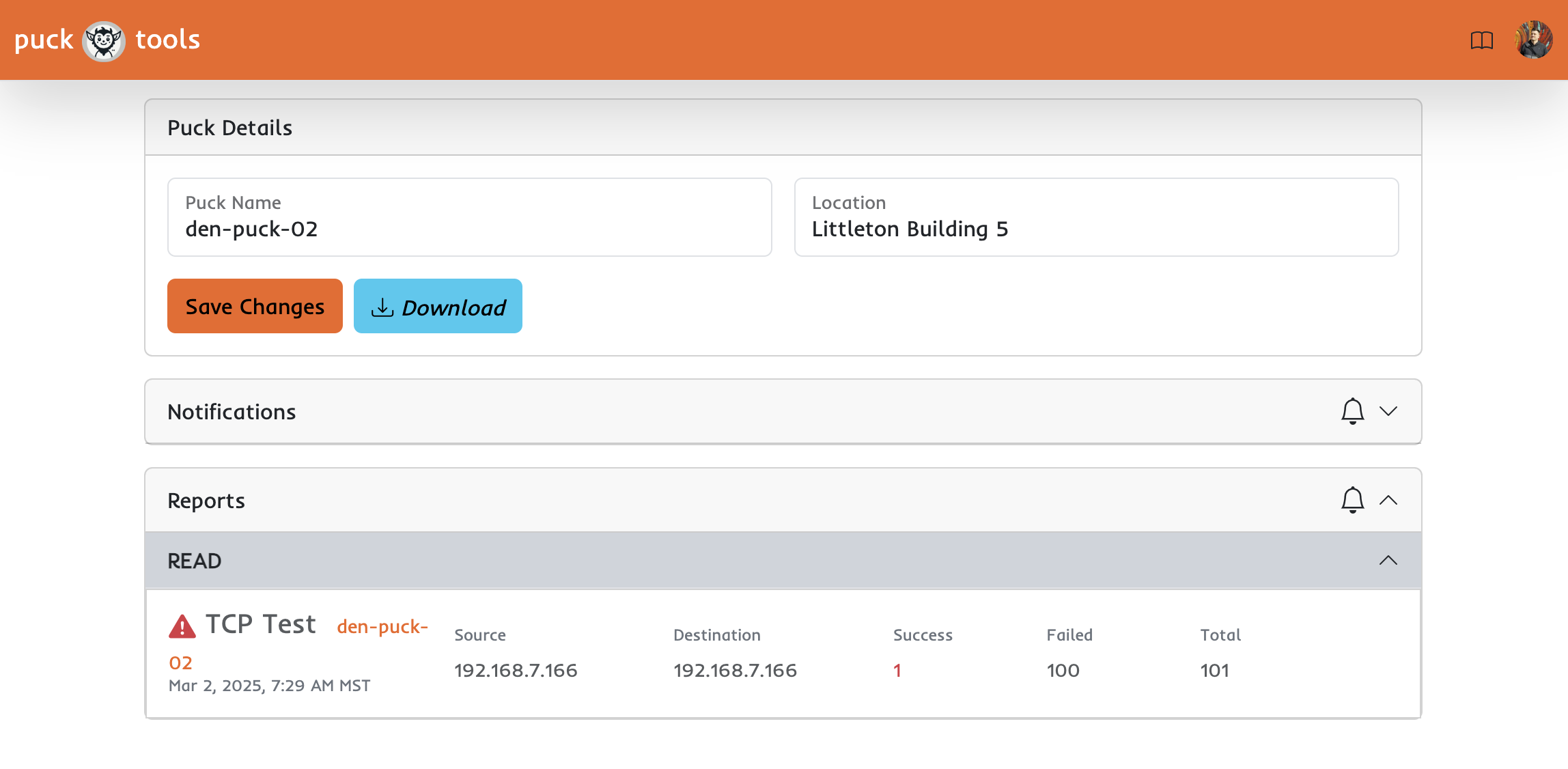
Puck Details Page
The puck details page lets you quickly manage and see historical results from tests conducted by individual pucks.
Key Capabilities
Secure Communication
The Puck Agent establishes secure, encrypted communication with the Puck Tools platform using:
- Strong Encryption: All communications are protected using ChaCha20-Poly1305 encryption with public/private key pairs
- Multiple Communication Channels: The agent can communicate through various protocols to ensure reliable operation in different network environments
- Resilient Connectivity: If one communication method is blocked, the agent can automatically switch to alternative methods
Network Egress Testing
The agent systematically tests outbound connectivity using methods that simulate how malware would attempt to establish command and control (C2) channels:
- TCP Scanning: Tests outbound TCP connections across both common and randomized ports
- UDP Scanning: Identifies available UDP communication paths
- HTTPS Testing: Verifies web-based communication channels that could be exploited
Network Segmentation Testing
Network segmentation testing validates that your internal network boundaries are working as intended by testing connectivity between deployed pucks. This simulates lateral movement attempts that an attacker might use after gaining initial access to your network.
How It Works:
When internal scanning is enabled, pucks attempt to communicate with each other across network boundaries:
- Listener Setup: Each puck listens on its configured internal ports (TCP and UDP)
- Connection Testing: Pucks attempt to reach other pucks on these listening ports
- Result Reporting: Successful connections indicate potential segmentation gaps
Understanding Listening Status:
In the Internal Port List view, each port shows its listening status:
- Green (Listening): The puck successfully bound to this port and is ready to receive connections
- Red (Unavailable): The port could not be bound, typically because another service is using it or the port requires elevated privileges
Supported Protocols:
Internal scans support the same protocols as egress testing:
- TCP Scan: Tests reliable, connection-oriented communication paths
- UDP Scan: Tests connectionless communication paths
- HTTP/HTTPS Scan: Tests web-based communication channels
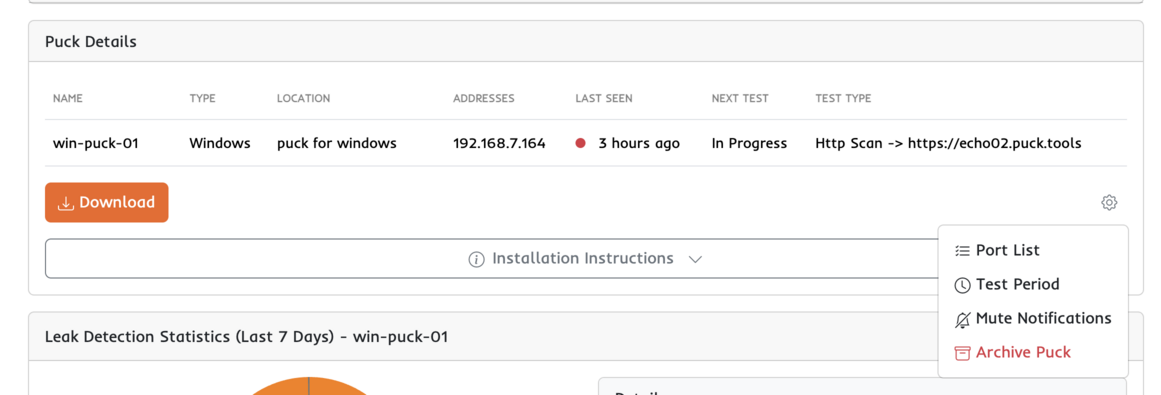
Customization
Most organizations can leave the puck configurations as is. The defaults are designed to be effective for a large majority of situations. If you do need to customize the tesing for your organization click the configuration button.
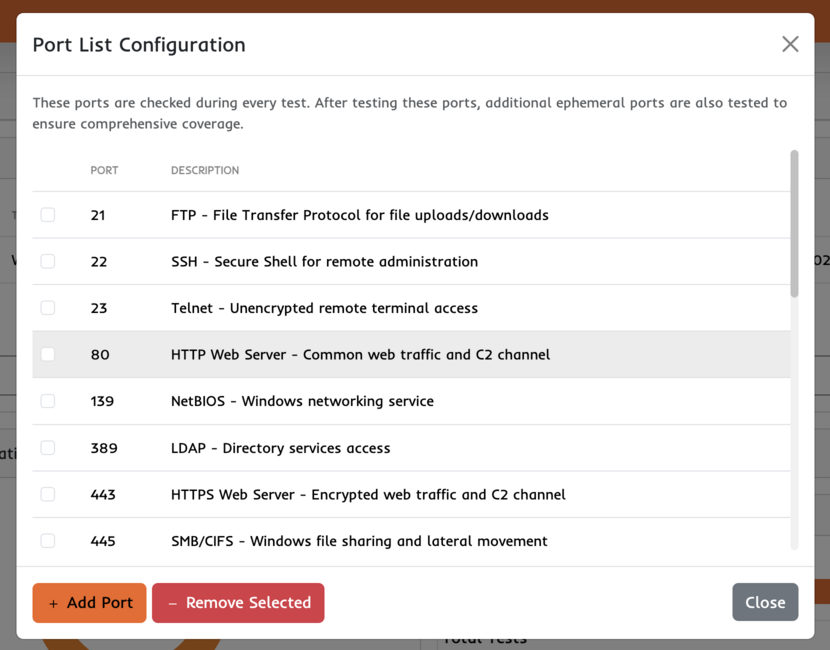
External Port List
By default each puck will start testing with a list of the most commonly exposed default ports. Then continue to lesser used ports until it hits 100 failures or finds 5 open ports. If you like to manage the default ports that are tested click the configuration button (the cog wheel) and select "Port List".
Internal Port List
Each puck attempts to listen on a default set of commonly used ports which allows the pucks to test network segmentation. This view allows you to quickly manage what ports will be tested and see what ports the puck is able to listen on.
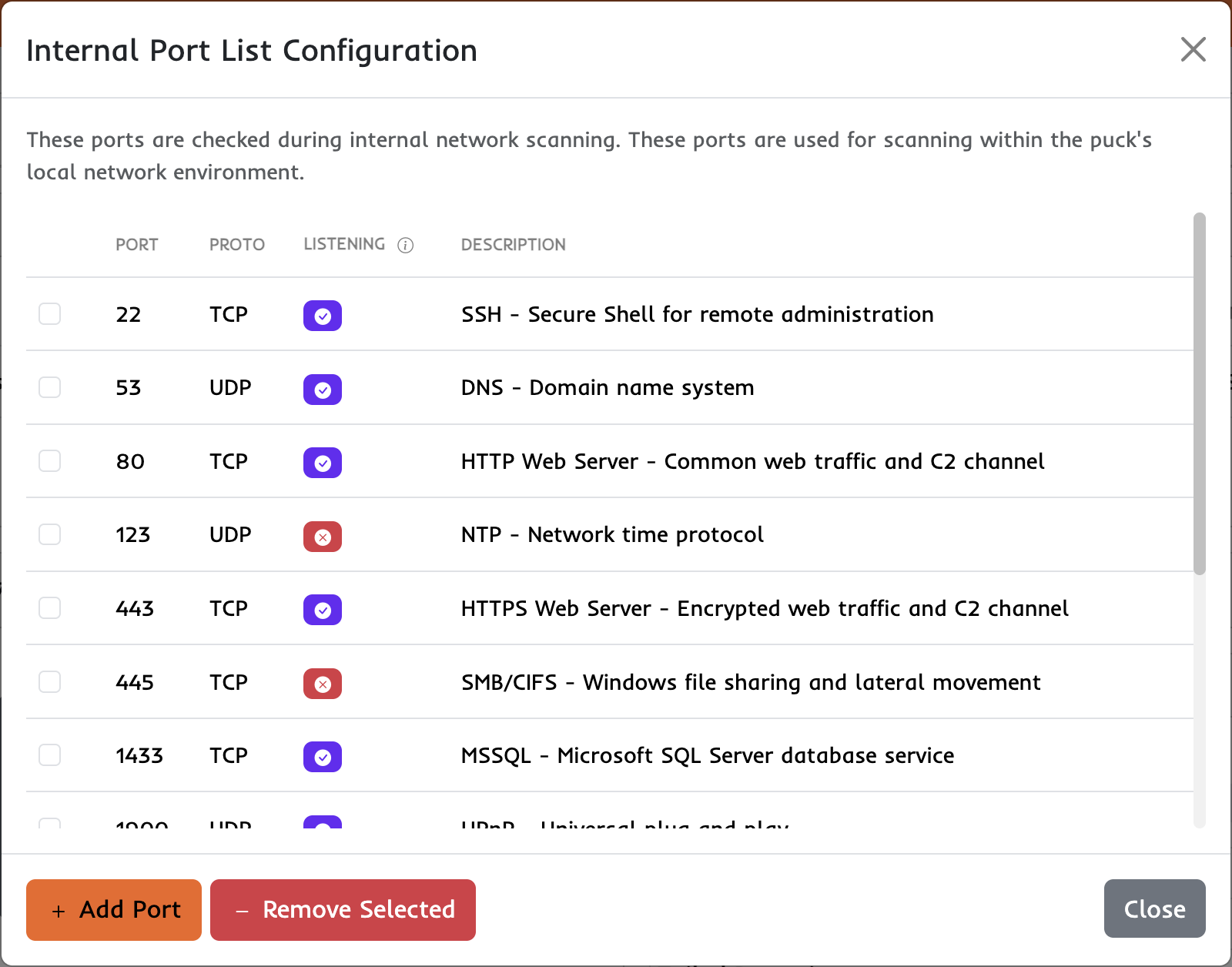
Managing Internal Ports:
To add or modify ports for internal scanning, click the "Add Port" button in the Internal Port List modal:
- Port Number: Enter a value between 1-65535. Ports below 1024 may require elevated privileges.
- Protocol: Select TCP or UDP depending on what type of traffic you want to test.
- Description: Add an optional description to help identify the purpose of this port (e.g., "SSH", "Database", "Custom App").
You can remove ports by clicking the delete icon next to any configured port. Changes take effect on the next puck check-in.
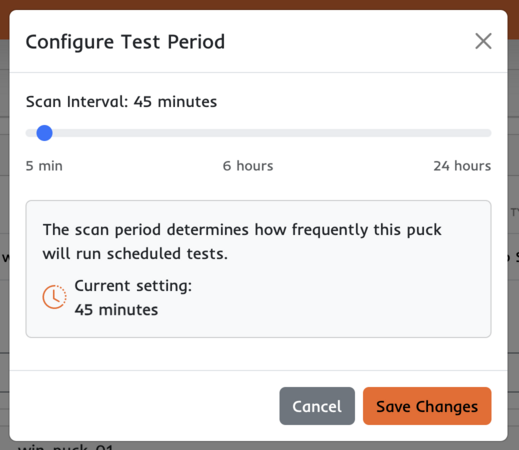
Test Period
Test period allows you to control how often tests are run.
Mute Notifications
Disable notifications for this puck. WARNING this option will not alert you if the puck finds an egress path.
Archive Puck
If you are done with this puck and would like to deploy a new version. You will still have access to historical test data, but tha puck agent will no longer successfully check in.
Safety by Design
The Puck Agent is built with safety as a primary consideration:
- Read-Only Operation: The agent cannot execute arbitrary commands on your systems
- No System File Analysis: The agent does not access, read, or analyze sensitive system or user files
- Controlled Testing: All network tests are performed in a controlled, non-destructive manner
- Minimal Resource Usage: The agent is designed to have minimal impact on system and network performance
How the Puck Agent Works
1. Deployment and Initialization
Once created, click the "Download" button and follow the simple install instructions. When deployed, the Puck Agent:
- Initializes with a secure configuration
- Establishes an encrypted connection to the Puck Tools platform
- Authenticates itself using unique identifiers
- Begins its testing cycle based on configured parameters
2. Testing Methodology
The agent employs a systematic approach to testing network egress paths:
- Prioritized Testing: Begins with common ports and protocols frequently used by malware
- Verification Process: For each potential path, the agent verifies bidirectional communication
- Comprehensive Coverage: Progressively tests additional ports and protocols to ensure thorough coverage
- Adaptive Behavior: Adjusts testing based on network conditions and previous results
3. Result Reporting
After completing its tests, the agent:
- Securely transmits findings back to the Puck Tools platform
- Provides detailed information about discovered egress paths
- Identifies which protocols and ports allow outbound connections
- Helps prioritize remediation efforts based on risk
See the Report Details page for more information.
Technical Insights
Malware Emulation Techniques
The Puck Agent employs several techniques commonly used by malware to establish outbound communications:
- Protocol Diversity: Tests multiple protocols to find available communication channels
- Port Scanning: Systematically checks ports that are commonly used for C2 communications
- Covert Channels: Tests methods like DNS tunneling that are often used to evade detection
- Persistence Mechanisms: Uses resilient communication methods to maintain connectivity
Security Considerations
While emulating malware communication patterns, the Puck Agent maintains strict security boundaries:
- No Payload Execution: Unlike real malware, the agent never executes malicious code
- No Data Exfiltration: The agent does not attempt to access or exfiltrate sensitive data
- Controlled Operation: All activities are limited to network testing with no system modifications
- Transparent Operation: All agent activities are logged and reported for complete visibility
Benefits for Security Teams
The Puck Agent provides several key benefits for security teams:
- Proactive Security Testing: Identify and address egress vulnerabilities before they can be exploited
- Firewall Validation: Verify that firewall rules and network segmentation are working as expected
- Continuous Monitoring: Detect changes in network configuration that could create security gaps
- Risk Reduction: Minimize the risk of successful data exfiltration or command and control establishment
- Compliance Support: Demonstrate due diligence in protecting against data exfiltration risks
Deployment Scenarios
The Puck Agent can be deployed in various scenarios:
- Internal Network Testing: Deploy across internal network segments to test segmentation
- Remote Worker Security: Test remote worker environments for potential security gaps
- Cloud Environment Validation: Verify security controls in cloud-hosted infrastructure
- Third-Party Risk Assessment: Evaluate partner networks for potential security risks
Conclusion
The Puck Agent represents a sophisticated yet safe approach to testing network security by emulating malware communication techniques without the associated risks. By identifying potential egress paths before they can be exploited, security teams can proactively address vulnerabilities and significantly enhance their organization's security posture.
For more information about deploying and using the Puck Agent in your environment, please contact our support team at contact@pucktools.com.